For Managed Service Providers (MSPs), delivering robust security and compliance in Microsoft 365 is...

In today's digital landscape, email remains the most widely utilized method of business-to-business communication. However, it also represents one of the most significant cybersecurity risks. From phishing attacks to ransomware and CEO fraud, the threats targeting email users are endless. This is where third-party email security solutions come into play, offering robust protection that goes beyond the limitations of standard email providers.
Email providers are responsible for the integrity of their code and platforms, but the responsibility for other threats and risks falls squarely on the user. Even Microsoft suggests seeking protection from third-party solutions, as they do not cover all aspects of cybersecurity risks in their user agreements.
Third-party email security solutions offer several advantages, such as:
24x7 IT Security: These solutions provide round-the-clock protection without requiring technical skills from users.
Central Management: A single pane of glass controls the entire organization's email security, including user access rights, archiving, data backup, auditing, and security awareness services.
Flexibility and Scalability: These solutions are designed to grow with your organization and can adapt to changing needs.
Cloud-Based Services: Offering full business continuity, these services ensure that your email communication remains secure and uninterrupted.

Establish your email security foundation with a multi-level filtering system, advanced encryption, and signature & disclaimer solutions to keep your email communication clean and legally compliant.
More than 50% of all email traffic is spam, meaning it is the most intrusive method cyber criminals use to introduce malware and viruses into corporate systems. In addition to the danger of infection with ransomware, spyware or a cryptominer, important workflows can also be interrupted by the annoying flood of unwanted spam emails. A multi-level filtering system in a must if you want to stop spam and phishing emails from reaching your inboxes and disrupting the workflows. And we have just the thing!
Cybercriminals are always seeking to tap into business emails containing sensitive and confidential information, whether to use them for spying or a successful cyberattack. With Hornetsecurity’s Email Encryption, you can rely on all-round encryption exchanges for secure email communication.
Companies need a professional look and consistent messaging across the entire organzation in external communications – something unified signatures and disclaimers can provide. Hornetsecurity’s Email Signature & Disclaimer are legally compliant and easy to set up, edit, and apply to all users (or sets of users) at once.

Stay ahead of cybercriminals with our premium next-gen protection with self-learning, AI-based filters and detection mechanisms, and benefit from additional features that ensure compliance and the maintenance and uptime of email communication.
Cybercriminals work tirelessly to develop new cyber threats, making it difficult for traditional security software to keep up and protect users from newly emerging attack methods. Ransomware, CEO fraud, spear phishing, blended attacks are just some examples of the dangers lurking in cyberspace.
With the rise of widely available AI tools, cybercriminals can effortlessly create flawless-looking phishing emails, and even bypass safeguards; they also use AI text-generating tools to create malicious codes.
With Advanced Threat Protection, you need not worry about any of the above. Using AI to its best advantage, Advanced Threat Protection keeps you ahead of cybercriminals, securing you from zero-day attacks and even the most sophisticated threats.
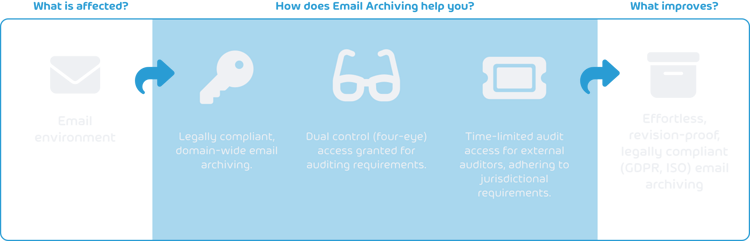
Archiving business emails is a legal necessity, with several requirements to be met. Archiving must be audit-proof and legally compliant, with appropriate retention periods set in place. Archiving-related admin tasks can be time-consuming, alongside customers needing a practical way to grant access to third parties to execute audits. This is where we come in.
Nobody ever expects a server failure, yet they can happen to anyone at anytime, causing huge disruptions in business operations. If you want to continue your operations regardless, you need a continuity service that activates automatically within seconds and synchronizes email data to be easily accessible and searchable. And we’ve got just the thing.
.png)
Set your mind at rest and avoid the impact of lost, damaged or deleted M365 data with automatic backups, robust and unlimited storage, and ransomware protection.
1 in 5 companies falls victim to a ransomware attack, with 15% of ransomware attacks specifically targeting backup storage. And those numbers can only get bigger as cybercriminals evolve their attack techniques and perfect them using AI tools. The costs of downtime and data loss can easily ramp up to millions.
Read more about the backup product on our dedicated Microsoft 365 backup page

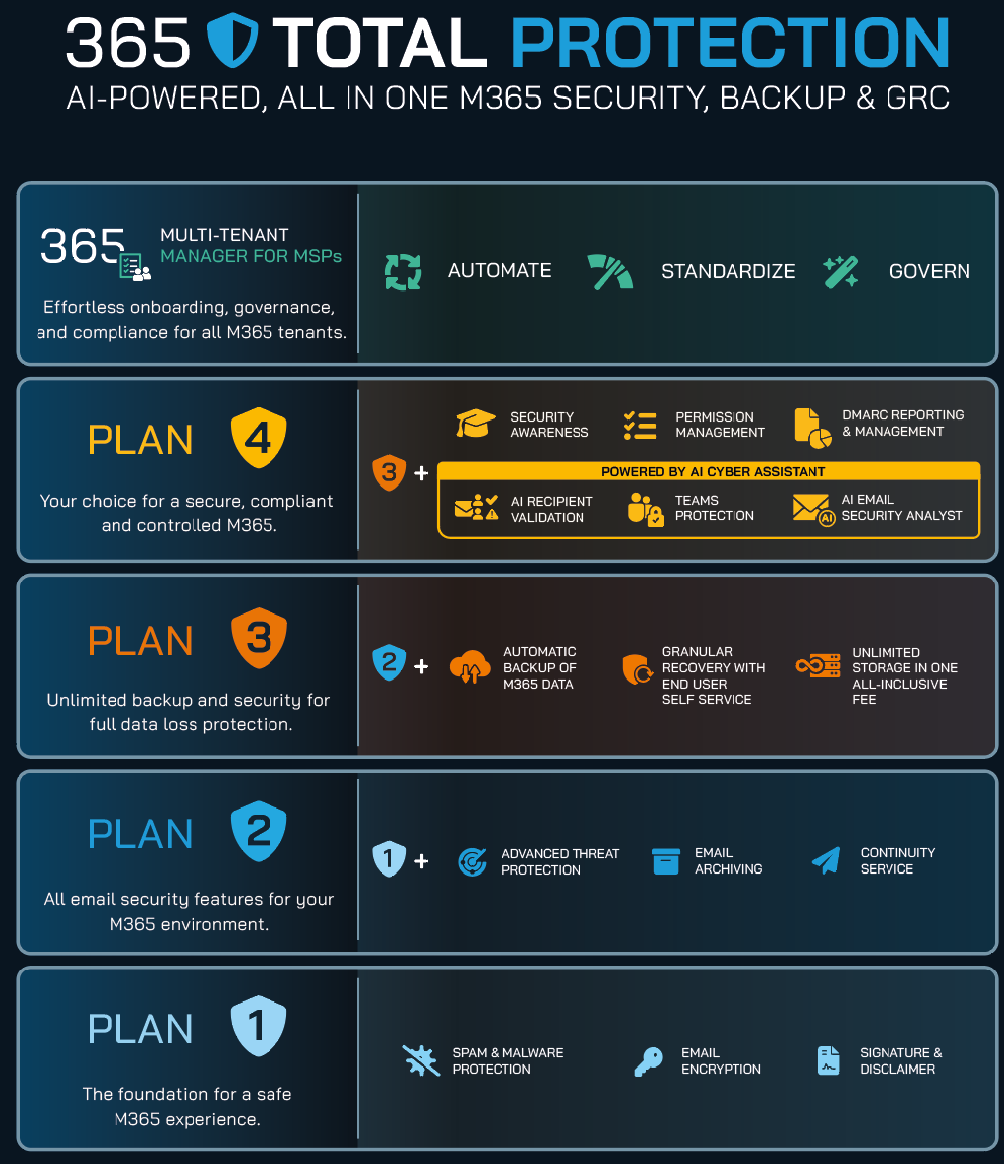
Streamline and bullet-proof your business operations with the most comprehensive Microsoft 365 solution on the market covering security, risk, governance, compliance, backup, and security awareness – in one package, on one license.
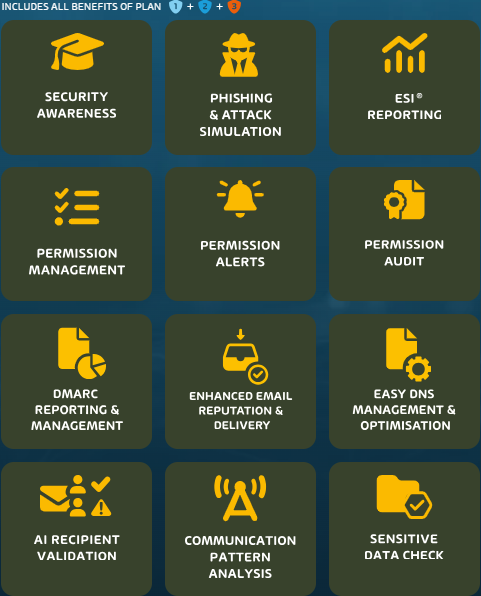
95% of all cybersecurity incidents are caused by human error, with the biggest weakness being email communication. Your employees are on the frontline when attackers try to exploit technical or human vulnerabilities. By training your employees, you reduce the risk of a successful breach.
Microsoft 365 offers many benefits, such as increased productivity and collaboration through Office 365, Teams, and SharePoint. It allows for real-time collaboration and easy remote working, with access to business data from anywhere.
But while users are enjoying a productive working environment, CISOs and M365 admins are losing control over file permissions and risking compliance violations which may result in security breaches, hefty fines and lawsuits.
Almost any domain can be spoofed by cybercriminals who then send fraudulent emails that appear to come from your organization. Using advanced artificial intelligence, cybercriminals can easily copy the look and feel of any company. This makes it increasingly challenging to spot forged emails. If cybercriminals use your identity for phishing emails, the consequences can be severe for your brand image.
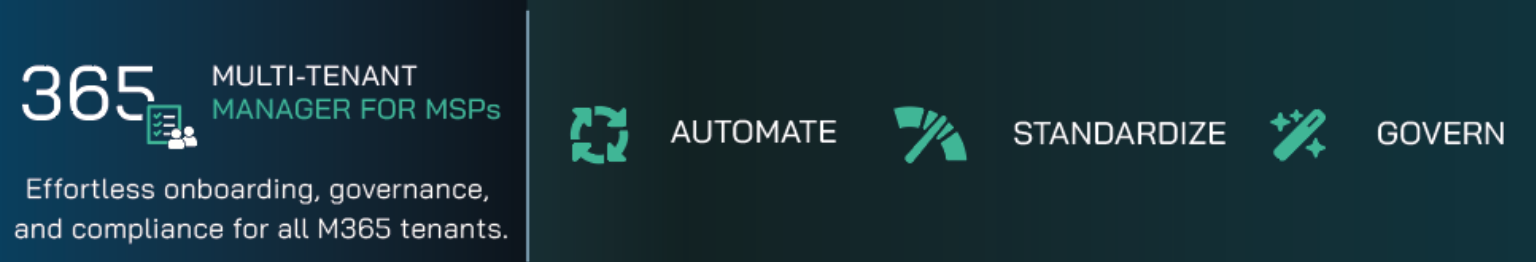
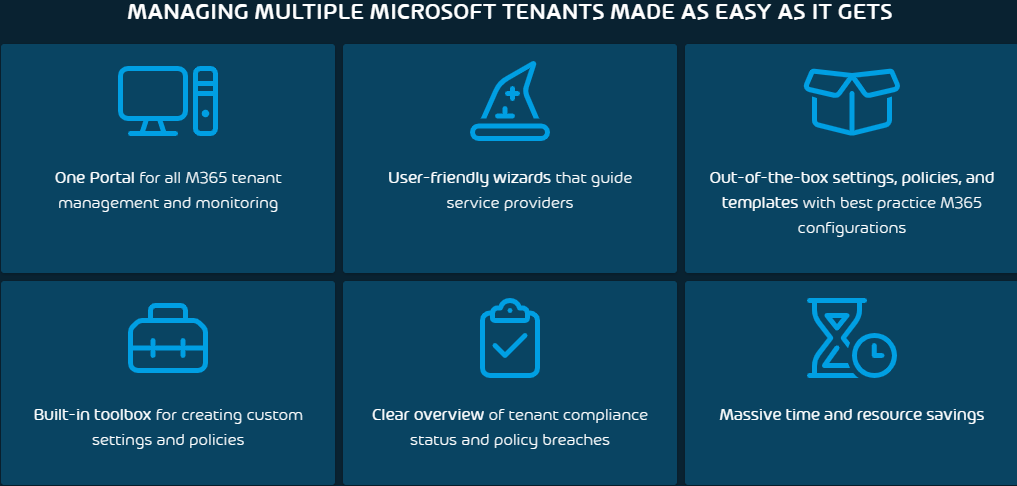
Stop manually onboarding and configuring all the different settings and policies across your Microsoft tenants and let 365 Multi-Tenant Manager for MSPs automate the daunting tasks for you.
Please Note that Multi-Tenant Manager is not included in Plan 4, it is licensed separetely for the MSP.
“ We found ARJ Distribution several years ago when we could not find a suitable software partner in Finland.
We have been very satisfied with the cooperation from the beginning, especially with the technical expertise.
This is one of the reasons why we have been able to help our own customers quickly and expertly.”

Do you want to expand your portfolio to include Hornetsecurity managed services? No problem – just fill out our online Partner Agreement and you will be part of the Hornetsecurity channel sales network.
Join our partner network here
Fact sheet for the new TP4 Plus that includes additional services such as AI Cyber Assistant, Teams Protection as well as AI Email Security Analyst
Download
With over 345 million paid seats globally, Microsoft 365 is a critical component of business operations for organizations of all sizes. But, keeping it secure is up to you.
Download
Fact sheet about the original Total Protection Plan 4, this is now known as Plan 4 LEGACY.
Download Product Fact Sheet
Do you know who has access to your companys M365 data? With Permissions Manager you can find out all shared links done from when you started to use M365, and configure policys and alerts to get control.
Ladda ner
Setup, manage and maintain e-mail authentication for your customers with DMARC Manager. An easy solution to configure DMARC, DKIM and SPF settings for your domains.
Download PDF
Hornetsecurity SAT solution educates your users in cybersecurity totally automated without adding a burden to the administrators or IT team.
Download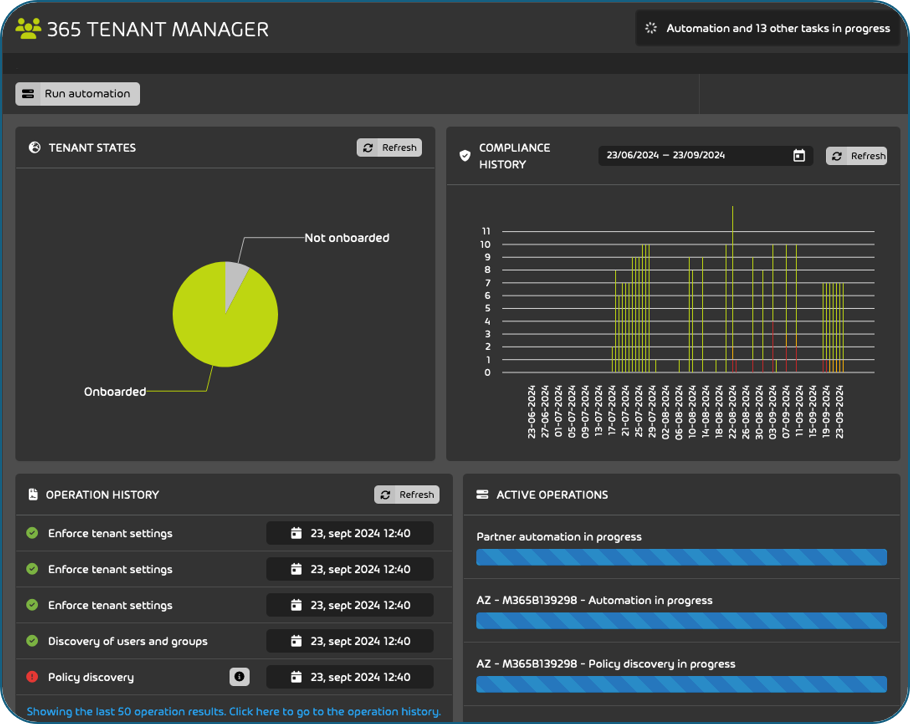
Work smarter, NOT harder! Stop manually onboarding and configuring all the different settings and policies across your Microsoft tenants and let 365 Multi-Tenant Manager for MSPs automate the daunting tasks for you.
Download
As a MSP you are managing multiple M365 Tenants at scale. MTM Can help you be more efficient and save valuable time.
Download
AI Cyber Assistant is your vigilant AI security booster that empowers end users and admins in their day-to-day operations, ensuring secure communication and a lighter workload.
Download One Page Overview
Thanks to growing media attention, end users are becoming increasingly suspicious of incoming emails. AI Cyberassistant can help you manage alerts more efficently.
Download AICA Value Proposition
Secure your users Microsoft Teams Sharing by scanning for malicious links and malware sent by either externally open Teams or compromised internal accounts.
Download Teams Protection Value Proposition
Hornetsecurity VM Backup is an intuitive and easy to use VM backup solution for VMware or Hyper-V hypervisors.
Read about it here
I detta dokument ser ni skillnaderna i funktioner emellan de olika versionerna.
DownloadIf you would like to signup for a trial of any of the Hornetsecurity solutions please use the button the the right,

For Managed Service Providers (MSPs), delivering robust security and compliance in Microsoft 365 is...
Written by Paul Schnackenburg / 26.03.2025 / Security Awareness

Why Use a Third-Party Email Security Solution? In today's digital landscape, email remains the most...